HFHE Key Sharding
The scheme and description below provide a visual example of how we divide keys and distribute them across nodes. The bootstrapping algorithm based on hypergraphs is not presented here, and all key features are generalized. The details of these important algorithms will be explained in subsequent articles.
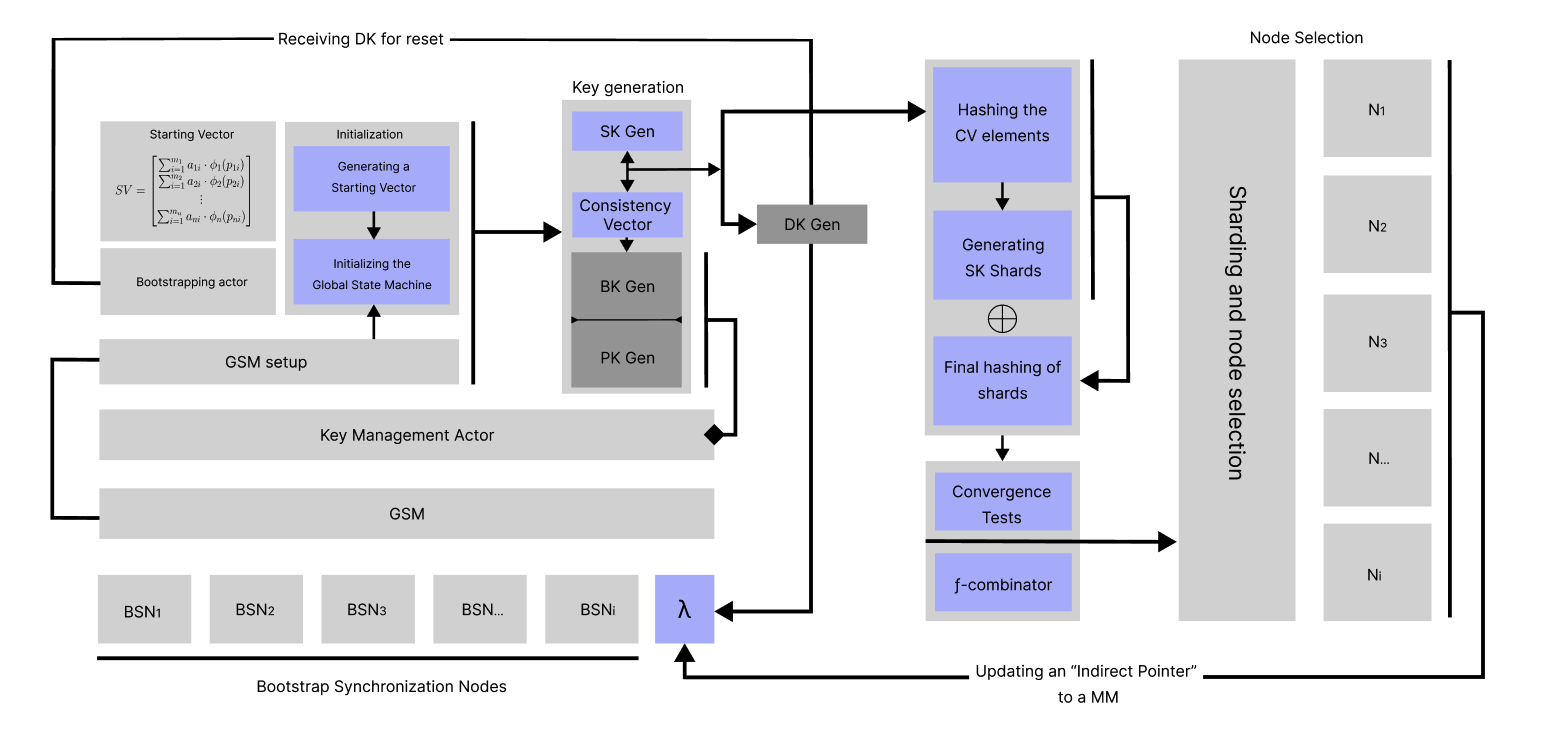
Schematic diagram of key sharding
-
Initialization The process of setting up the Global State Machine (GSM) and generating the Starting Vector.
-
Starting Vector (SV) The initial vector derived from key components, used as the foundation for further cryptographic processes.
-
Key Generation
- SK Gen Secret Key Generation process where the starting vector is hashed and transformed into the secret key.
- Consistency Vector A transformation of the Secret Key that is used in the generation of other keys.
- DK Gen Decryption Key Generation where the Decryption Key is derived from the Secret Key and Consistency Vector.
- BK Gen Bootstrapping Key Generation for noise reduction in ciphertexts.
- PK Gen Public Key Generation for encryption, which will be shared with users for secure communication.
-
Hashing the CV elements The process of hashing elements of the Consistency Vector for shard generation.
-
Generating SK Shards The operation where the Secret Key is split into shards for distribution.
-
Final hashing of shards The last step of hashing each shard for additional security before distribution.
-
Convergence Tests Tests to ensure that the shards can be recombined to recover the original Secret Key.
-
ƒ-combinator A function that prepares sharded keys for node allocation, confirming their integrity and recoverability to ensure the original Secret Key can be accurately reconstructed from the shards.
-
Node Selection The process of selecting nodes for shard distribution, ensuring data resilience and security.
-
GSM The Global State Machine which maintains the state of the system.
-
Bootstrapping actor The entity responsible for initiating the bootstrapping process.
-
Key Management Actor The component that manages the lifecycle of keys including generation, rotation, and retirement.
-
Bootstrap Synchronization Nodes Nodes responsible for synchronizing the bootstrapping process across the system.
-
Receiving DK for reset The step where the Decryption Key is received for the purpose of resetting or reducing noise in the ciphertexts.
-
Updating an “Indirect Pointer” to a MM The action of updating an indirect pointer within the Global State Machine.
Description of the methods used
The Starting Vector is a structured array where each element is a sum of products of coefficients and the respective transformed parameters.
Keys generation process
Secret Key Generation
The Secret Key is generated by hashing the XOR-ed result of each Starting Vector element . after applying an S-box transformation and an additional XOR with coefficient .
Consistency Vector Generation
The Consistency Vector is created by transforming each element of the Secret Key through multiplication with a corresponding large prime and addition of a shift factor.
Bootstrapping Key Generation
The Bootstrapping Key is obtained by XOR-ing all elements of the Consistency Vector, used in the noise reduction process during decryption.
Public Key Generation
The Public Key is derived by applying a modular operation to each element of the VC, followed by an addition of an offset, then combining the results using XOR.
Decryption Key Generation
The Decryption Key is generated by hashing the combined value of the Consistency Vector, the Secret Key, and the product of VC with a large prime, using the Blake 3 hash function for high security.
Sharding and node selection
Hashing the Consistency Vector Elements
Each element of the Consistency Vector is hashed using the Blake 3 cryptographic hash function, taking corresponding elements of the Secret Key as input.
Generating SK Shards
Secret Key shards are generated by hashing the XOR of each Consistency Vector element with a unique salt using Blake 3, ensuring unique and secure sharding.
Final Hashing of Shards
The final hash of each Secret Key shard is computed using Blake 3 to provide an additional layer of security, resulting in the final shard ready for distribution.
Node selection
The final selection of the node for each is based on the highest calculated value from the given expression.
The node selection is determined through an optimization process that identifies the node with the maximal value of a predefined evaluative function, ensuring an optimal choice based on specified criteria for each index
Some critical elements such as the ƒ-combinator and Hypergraph Bootstrapping, key management actors, bootstrap node management actors, and noise level assessment are addressed in separate articles.
Last updated 2 months ago